Expert Perspectives from Montra
Montra executives, subject matter experts, and independent authorities provide insights and commentary on the key issues that matter most to you and your business.
From Challenge to Success: Navigating Identity Lifecycle Management for Tech Companies
As the digital footprint of businesses diversifies, Identity Lifecycle Management (ILM) plays a crucial role in enhancing security, ensuring compliance, and improving operational efficiency. Read about the challenges and keys to success for tech companies implementing ILM.
The Evolution of IT Asset Management Software in 2024: Converge the Data
As IT asset management continues to evolve, it increasingly intersects with adjacent domains such as device monitoring, device security, and inventory management. We examine here the latest trends shaping asset management software in 2024, examining notable advancements, emerging features, and evolving end-to-end processes.
Device Protection 101: Safeguarding Businesses through Effective Device Monitoring
Businesses are increasingly reliant on technology to optimize business operations and stay competitive. Let’s delve into the top 5 ways monitoring devices can elevate your business’s protection levels and empower your workforce, especially ensuring uptime, availability, security, and compliance.
Four Ways to Revamp IT Rollout Efficiency for Retail
Retailers, in their effort to modernize, encounter a formidable challenge. Implementing new technology across numerous stores has unique configuration requirements.
Three Obstacles to Better IT Onboarding and How to Avoid Them
Discover how embracing advanced IT onboarding solutions can mitigate common onboarding challenges, paving the way for seamless integration of new employees into the workforce.
Identity Lifecycle Management in the Modern Enterprise: The What, Why and How
In today’s digital landscape, where data breaches and cyber threats are prevalent, businesses are increasingly focusing on Identity Lifecycle Management (ILM) to safeguard their sensitive information and ensure secure access control. ILM is the process of managing user rights to systems, applications and data, over time as their roles evolve in an organization.
Send Them on Their Way: The Benefits of Automating Your IT Offboarding Process
Saying goodbye can be tough, especially when it comes to offboarding employees. There’s paperwork to collect, access to revoke, and a multitude of other tasks to complete. And, let’s be honest, no one wants to waste their time on a process that’s notorious for being bureaucratic and time-consuming.
Four Benefits of Outsourcing Your IT Logistics Processes
IT logistics is the set of process a business must execute to securely and efficiently deploy and manage IT devices in their operations.
Montra Included in Atlanta Inno 2023 Fire Awards
Montra has been identified by Atlanta Inno as one of 25 Atlanta companies as an honoree in their 2023 Fire Awards. The Atlanta Inno team considered factors such as funding, revenue growth, mission and future potential when selecting the finalists.
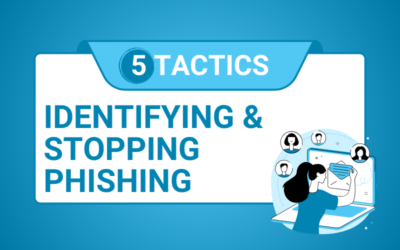
Identifying and Stopping Phishing Attempts: 5 Tactics
We go over five tactics to identify and stop phishing – a common tactic for cybercriminals to gain access to your organization’s sensitive data.
Laughing at Hackers: 5 Proactive Steps You Can Take to Secure Your Laptops from External Threats
Here’s a joke that’s not funny: your company’s data was just hacked. Shock waves, unmitigated panic, and alibis are all fair play when you as the CIO, CISO or Head of IT, wakes up to the news that a hacker has infiltrated their systems.
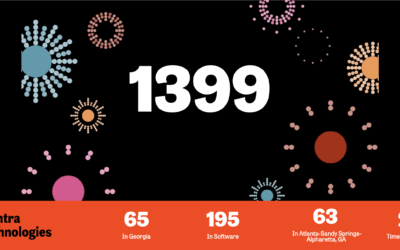
Montra Continues Growth and Moves Up the 2023 Inc. 5000
Montra ranks No. 1,399 on the 2023 Inc. 5000, its annual list of the fastest-growing private companies in America and is among the top 200 software companies in the United States.
The Basics of Unified Communications as a Service: A Crash Course for Business Leaders
As a business leader, you know that communication is key to success. In this post, we’ll give you a crash course on the basics of UCaaS, so you can determine if it’s the right fit for your organization.
Why a Cybersecurity Compliance Program is Necessary for Every Business
As a leader, you are responsible for ensuring that your organization’s data remains secure and protected from cyber threats. Cyber-attacks can result in the loss of millions of dollars, loss of customer trust, and reputational damage from which it can take years to recover.
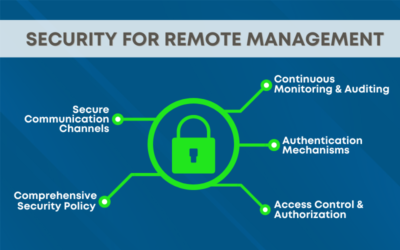
Remote Management System Deployment: Beware of the Security Risks
Remote management systems have evolved into a valuable tool for IT professionals, enabling remote access, monitoring, and management of their organization’s IT infrastructure. However, as with any technology, they come with inherent risks.
How Hybrid Work is Affecting Remote IT Management: A Crash Course
As the world continues to adapt to the changing landscape of work, the concept of hybrid work has emerged as a popular model for many organizations. Hybrid work combines elements of remote work and in-person collaboration, allowing employees to have flexibility while also maintaining some level of face-to-face interaction.
Montra Releases Notable Updates To Its IT Management Platform
Today, Montra announces updates to its award-winning platform, providing customers with improved navigation and an increased breadth of available features.
Leveraging Technology to Enhance IT Onboarding
Employee onboarding is a crucial process for any organization, and it’s especially important for the IT department. However, onboarding is often a lengthy and complex process, and without the proper tools and resources, it can be difficult to get new hires up to speed quickly.
Montra Expands Customer Base with Addition of Discovery Storage
Montra announces today it has signed Discovery Storage as a new customer, handling the company’s distributed IT management needs.
Mastering IT Logistics Management: 5 Things Retailers’ IT Asset Tracking System Should Deliver
Read this article from Retail Info Systems about Mastering IT Logistics Management: 5 Things Retailers’ IT Asset Tracking System Should Deliver
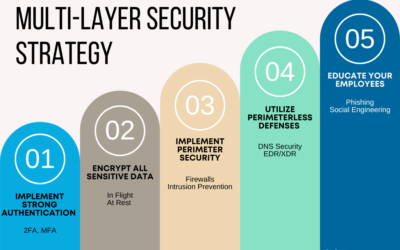
Cyber-readiness Strategy 12: Multi-Layer Security Strategy
Security is asymmetrical. Where businesses must plan, prepare and defend against every threat or scenario, cybercriminals only need to find a single weakness or hole in your defenses to carry out their malicious plans. Protect your data and your business by deploying multiple security strategies together as one.
Montra Makes the 2022 Inc. 5000 in First Year of Eligibility
Inc. has revealed that Montra, innovator of advanced remote IT management solutions for today’s workplace, is No. 1,976 on its annual Inc. 5000 list, the most prestigious ranking of the fastest-growing private companies in America.
Cyber-readiness Strategy 11: Reduce Supply Chain Vulnerabilities
Cybersecurity threats to the global supply chain can come from anywhere in the world, and they can have a devastating impact on businesses of all sizes. Increased digitization of the supply chain makes it all the more vulnerable.
Montra Ranked on Channel Futures 2022 MSP 501
Montra Ranked on Channel Futures 2022 MSP 501—Tech Industry’s Most Prestigious List of Managed Service Providers Worldwide
Benefits of Microsoft 365 and Azure Active Directory for Identity Management
Identity management is critical for businesses today. In a world where more and more employees are working remotely and accessing corporate data from a variety of devices, it's important to have a...
The Top 5 Benefits of Azure Active Directory
Are you looking for a comprehensive identity management solution? If so, Azure Active Directory (Azure AD) may be the perfect option for you. Azure AD is a cloud-based service that provides identity...
Laptop Security Best Practices
Laptops are a valuable asset for the workforce of companies of any size. They allow employees to stay connected while on the go and can are critical tools to accomplish work quickly and effectively....
Cyber-readiness Strategies 9 and 10: Passwords and Insurance
It's becoming increasingly difficult to keep up with the cyber security threats out there. From ransomware and phishing to malicious insiders and business email compromises, there are many dangers...
Three Tips to Improve HR and IT Process Integration
When it comes to discussing employee onboarding and offboarding there are two main players who are involved in the process, HR and IT. Often HR and IT professionals find themselves at odds with each...
Policies Management in Microsoft 365
One of the great benefits of Microsoft 365 is the robust policy-setting capabilities within the platform. You can have the best security features, the most user-friendly Wi-Fi setup, and the most...
Checklist for IT Employee Offboarding
Whether an employee leaves a company of their own accord or not, they first must be offboarded to ensure an easy and secure transition from their current role to their next one. IT administrators...
7 Step Checklist for Secure and Reliable Laptop Imaging
Your company’s laptops are a valuable business tool that enables the success of your workforce. It contains important information and files that are necessary for your work. That's why it's...
TAG Announces the Top 40 Innovative Technology Companies in Georgia
Media Contact: Russ Davis – russ@tagonline.org (404) 920-2023 TAG Announces the Top 40 Innovative Technology Companies in Georgia ATLANTA (April 13, 2022) – Each year, the Technology Association of...
12 Cyber Readiness Strategies #7 and #8
In our last blog post, we discussed cyber readiness strategies: #5 Back-Up Everything and #6 Don't Neglect Compliance. Continuing our series this week are discussing strategies #7 and #8, Continuous...
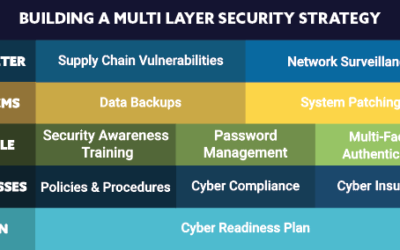
Building a Multi-Layer Security Strategy Infographic
Building a Multi-Layer Security Strategy Is your business ready to handle a targeted cyber-attack? Maybe you have been attacked and don’t even know it. According to the 2020 Thales Data Threat...
Six Steps to Successful Employee Offboarding
When an employee leaves a company, offboarding is the process of ensuring that they have a smooth and secure transition from their current role to their next one. This includes tasks such as...
Microsoft OneDrive – Eight Ways to Get the Most from It
When it comes to file storage and sharing, there are a lot of different options out there. Microsoft OneDrive is a cloud-based storage and synchronization service offered by Microsoft. It allows...
Seven Practices To Improve IT Asset Logistics
Do you know where all your company's IT assets are? If not, you're not alone - many businesses find it difficult to track down every phone, computer, or software license. IT asset tracking is an...
12 Cyber-Readiness Strategies #5 and #6
If you're like most IT professionals, you're always looking for ways to improve your organization's cyber-readiness. And rightly so: the stakes are high, and the threats are constantly evolving. In...
Five Easy Steps to Great Employee IT Onboarding
Contrary to common belief, the employee onboarding process isn’t just for HR. Most modern businesses are heavily reliant on IT infrastructure for client and team communication, employee and task...