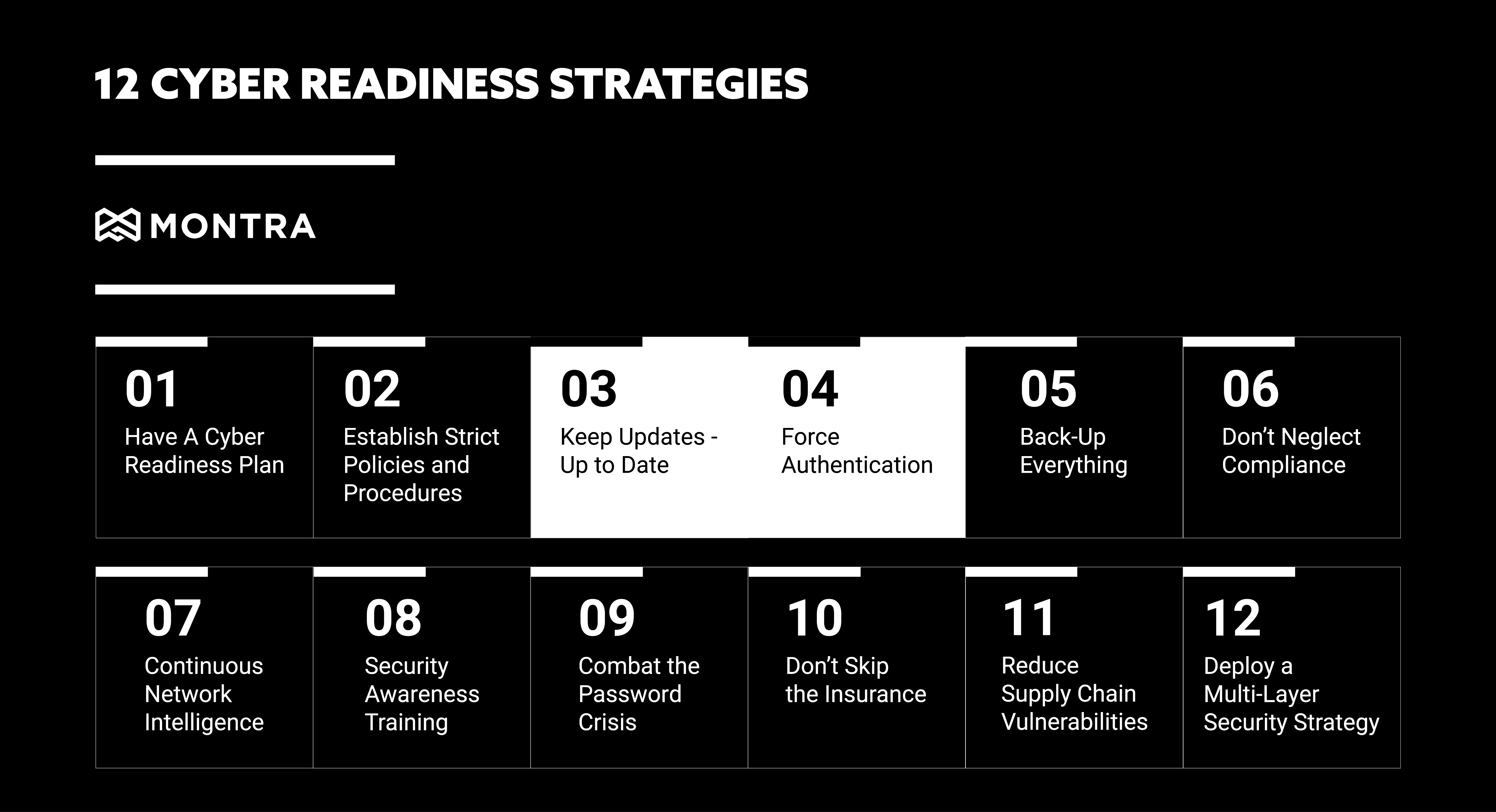
7 Step Checklist for Secure and Reliable Laptop Imaging
Your company’s laptops are a valuable business tool that enables the success of your workforce. It contains important information and files that are necessary for your work. That’s why it’s important to have a setup and a backup plan for your laptop imaging. In this blog post, we will discuss the best practices for laptop imaging so that you can keep your company data private and secure. When onboarding an employee, it is essential to set up their device and make sure to securely delete everything if a previous employee had that device. Laptop imaging can vary from business to business, so it is important to include specific instructions when onboarding a new user.
1. Start with a Fresh Image
It can be tempting for companies to try to skip the imaging process when deploying new or re-used laptops. By starting with a newly imaged device, companies can document updates and changes more effectively, and avoid accidentally duplicating bad software or private data. In addition, starting fresh provides an opportunity to review and improve upon existing processes. It may take some extra time up front, but the long-term benefits of starting from scratch are typically worth the investment.
2. Identify User Profiles
When it comes to information management, one size does not fit all. That’s why it’s important for companies to tailor their systems to the specific needs of each team or department. Accounting departments, for example, have very different needs than design centers. As such, it is often useful to create different master PC images for each department. This helps to optimize workflow and ensure that employees have the programs, permissions, and privileges they need to do their jobs effectively. While it takes a bit of effort to set up separate images for each department, the benefits can be well worth the investment.
3. Verify Device Compatibility
Not every PC Image will work for every workstation. Therefore, it’s crucial to consider things like computer type, hard drive capacity, RAM, graphics processing power, operating system, and compatible software before beginning. This is because something as simple as a system update can render some programs obsolete. By taking all of these factors into account, you can ensure that your Master Image will be compatible with all of the systems it needs to be used on. In doing so, you’ll save yourself a lot of time and headache in the long run.
4. Create a Master Image
With deployment criteria validated, IT technicians can initiate a Master Image. There are many programs available to facilitate the creation of a computer image, and IT professionals should determine which one is best suited for a company’s needs. Before deploying a PC image, technicians should patch the Operating System (OS) to ensure images are as up to date as possible. Next, technicians should install and update applications relevant to the target user’s system and configure appropriate permissions and privileges.
5. Maintain Drivers
Device drivers are programs that control devices connected to a computer. In most cases, devices are connected directly to the computer via cables, but they can also be connected wirelessly. Drivers allow the computer to communicate with the device and to use its features. For example, a printer driver allows the computer to send data to the printer so that it can print it. Drivers are generally specific to a particular make and model of device, and they need to be kept up to date to work correctly. When technicians update a computer’s operating system, they typically also update the device drivers. This ensures that all the devices will continue to work correctly with the new operating system. Technicians should double-check that all drivers are up-to-date and functioning correctly before updating any computer image.
6. Audit Master Image Regularly
Companies should develop a process for keeping the master image optimized. A best practice is to schedule a monthly audit of master images to ensure programs, permissions, and privileges are functional and current. This practice helps minimize the number of system updates and configuration changes needed each time imaging is applied.
7. Document Changes
Companies should remain diligent about documenting changes or updates to any Master Image. Proper documentation can save IT departments hours of headaches by simply noting the date of image, base configuration, and changes since the last version.
While this laptop imaging checklist only features the high-level steps for internal IT departments to consider, it should give you a general framework for simplifying the deployment of multiple devices. Organizations should reference this imaging checklist throughout their planning and strategy phases to develop realistic timelines and budgets.
Laptop imaging is a vital part of keeping your company’s data private and secure. By following the best practices for laptop imaging, you can ensure that your data is protected in the event of an employee departure, hardware return, or other change of control incident. If you need help with setting up laptop imaging for your business, contact our experts today at sales@montra.io