The past two years have had a major impact on everyone’s lives, so we are looking forward to 2022 with anticipation (well, not as much as the anticipation last year leading into 2021.) Some of the biggest changes as it relates to work have been in how and where we work, the increasing number of cybersecurity threats, and the changes in how IT services are delivered. As we look forward to 2022, we can see that these trends will have a big impact on how and why companies manage their employee information.
Employee information management is an important topic for a lot of mid-sized companies, especially those that are experiencing or are planning for a lot of growth. Running efficient on-boarding and off-boarding processes, keeping track of the latest employee information, and maintaining proper access to the right systems and services, are all functions impacted by good employee information management.
One of the challenges for businesses with their people information management is that there are islands of data on employees and contractors that exist within most organizations. Recruiting databases, HRIS, email systems, physical security access systems, finance systems, and other services, all maintain subsets of data on employees. Due to security and privacy concerns, it is difficult to access and update all these systems either by employees or by the admins. Additionally, the systems almost never talk to each other to synchronize changes.
This leads to three critical areas of concern with poor employee information management:
1. Employee Onboarding Takes Too Long: it takes longer to get new employees operational and effective
2. Security Risk is High: it is difficult to track employee credentials across all the systems and services for which they should be granted access
3. Employee Data Gets Stale and Inaccurate: Applications that rely on this data – like disaster recovery services – can become completely ineffective.
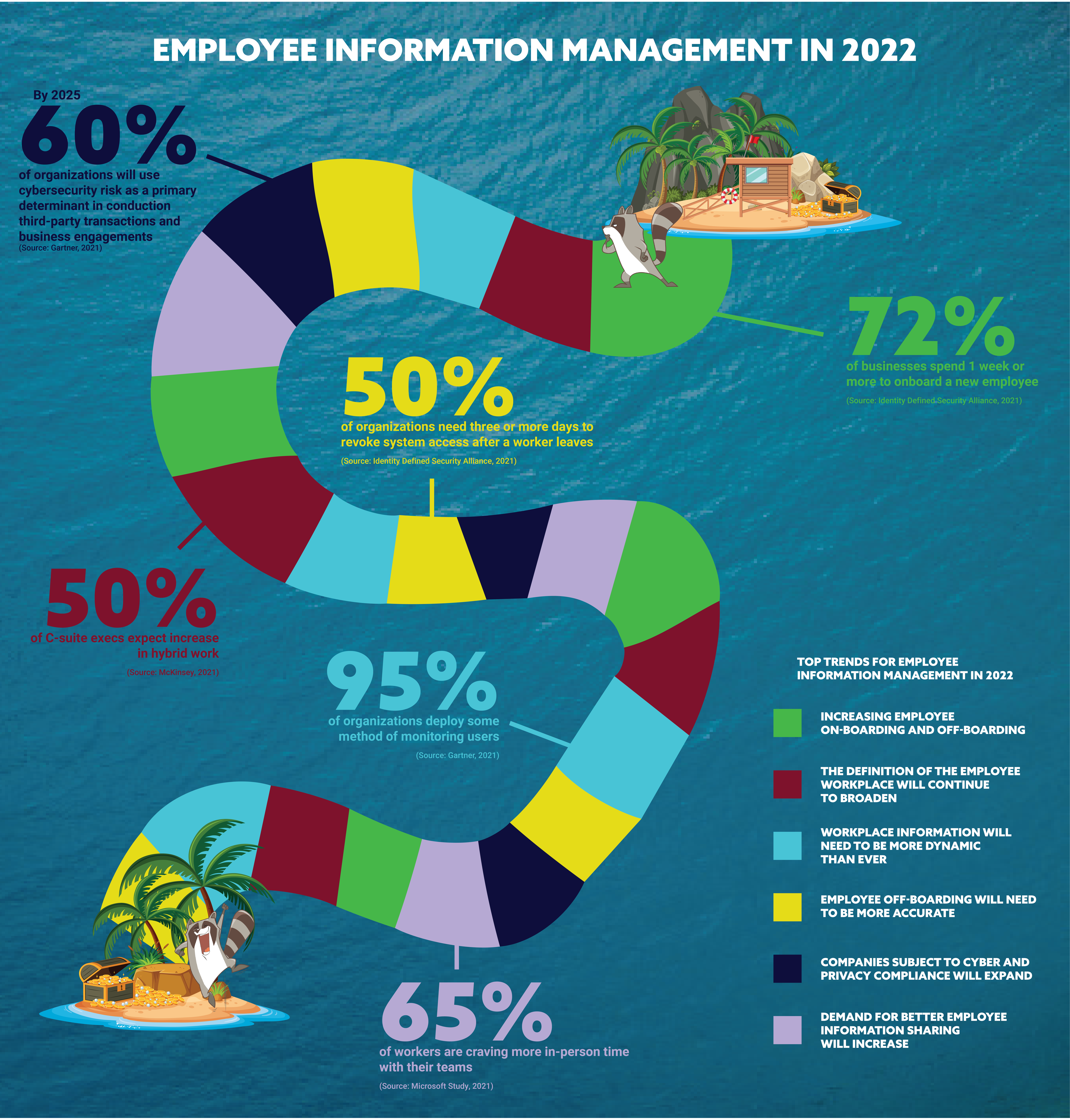
With that in mind, here are our top trends for Employee Information Management in 2022:
1. Increasing Employee Churn Will Drive Need for Better Employee Onboarding / Offboarding
The economy will continue its post-lockdown expansion. This will continue to fuel the higher rates of employee departures and arrivals than ever before. Employers are more pressured than ever to make certain the onboarding process is as quick and accurate as possible, while the offboarding process is secure and trackable for cybersecurity and compliance purposes.
2. The Definition of the Employee Workplace Will Continue to Broaden
The workplace has been changed forever over the past couple of years. More employees are working at home, in a co-working space, or even a in a second home away from major cities. What used to be a special case (“We have 3 offices and a few people that work from home.”) will continue to move toward the norm in 2022. Systems that track employee location today are almost all static and assume that a limited number of workplace addresses exist. Employers need to rethink what an employee workplace is and how they plan to handle this more dynamic and fragmented nature of the workplace.
3. Workplace Information Will Need to Be More Dynamic Than Ever
Understanding where an employee is, was, and will be, will become critical for company IT staff and others needing accurate workplace information in 2022. For cybersecurity policies and compliance to work properly, accurate information about a person’s location is needed. Different access policies can be enforced, and audit trails can be created to trace issues when they occur. Additionally, in the case of a disaster or other emergency, employers can know who was in what workplace and how notifications and recovery processes should be handled.
4. Employee Offboarding Will Need to Be More Accurate
Most mid-sized and high-growth companies do not well-run offboarding processes. With more employees leaving a company, any inefficiencies in the offboarding process will get exposed in 2022. In the past when a person was exited, the accuracy of removing access to every system was not that critical. If physical access to the building and email access was removed, offboarding was “80% done”. The rest of the systems could be updated at leisure. The modern workplace in 2022 will drive the need for accuracy. Enabling this means employee information about account and systems credentials needs to be accurate and easily accessible to the appropriate people. If the information is accurate, the former employee could have access to data or services that put the company at risk.
5. Companies Subject to Cyber and Privacy Compliance Requirements Will Expand
In 2022, expansions to the compliance requirements in HIPAA, PCI-DSS, CCPA, and GDPR, will pull more companies under the cybersecurity compliance and data privacy umbrellas. The definition of “third party” has now been expanded to “fourth party” in these frameworks, which broadly expands which companies must comply. Think “Six Degrees of Kevin Bacon” but a lot less fun. So even if your company isn’t specifically in the healthcare business, if your company does business with a company that does business with a company in healthcare, then your company may be subject to HIPAA.
6. Demand for Better Employee Information Sharing Will Increase
With all these employees working from home or in smaller satellite offices, what happens to the serendipitous interactions that happen in larger centralized workplaces? What happens to the friendships and even marriages that routines developed in the workplace of the past? Collaboration tools like Zoom and Slack exist already to make communication happen easily and quickly, but the tools to enable the sharing of deeper information are almost non-existent. Think: LinkedIn but for internal use only. Enabling employees to publish workplace relevant information and search on the information of others will spike in demand in 2022. This new area will continue to expand and evolve as the need for better familiarity and collegiality will be needed to enable better teamwork.
Download our Employee Information Management Infographic here
What do you think about managing your employee information? How do you think it will change in 2022? Let us know what you think at info@montra.io.