From Challenge to Success: Navigating Identity Lifecycle Management for Tech Companies
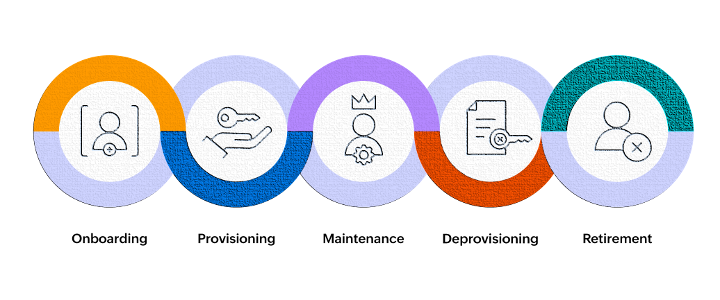
In today’s fast-paced digital landscape, managing user identities efficiently and securely has become a cornerstone for business security and productivity. Identity Lifecycle Management (ILM) is a comprehensive approach that governs the creation, maintenance, and deletion of user identities across an organization’s IT infrastructure. As the digital footprint of businesses diversifies, ILM plays a crucial role in enhancing security, ensuring compliance, and improving operational efficiency.
The market for Identity Lifecycle Management market was estimated at around $3-5 billion in 2023 with an expected CAGR of 12-14% over the next 5 years (Sources: Gartner, Allied, Fortune, Grand View). This growth is driven by increasingly stringent regulatory requirements like the General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) . Additionally, demand is driven by escalating cybersecurity threats. In 2023, the estimated global cost of cybercrime was approximately $8.4 trillion, according to various industry reports. By 2025, this figure is expected to reach $10.5 trillion annually, as forecasted by Cybersecurity Ventures.
Finally, the adoption of SaaS and Cloud technologies, the increasing amount of hybrid work, and the growth of IoT and connected devices, has created additional demand for ILM as organizations prioritize securing their digital assets and data no matter where their workforce may be.
Security and Management Challenges in ILM
No matter what the industry, managing an effective ILM process presents some significant challenges to IT departments.
Complexity of Integration
Implementing ILM solutions can be a daunting task, especially when integrating with existing legacy systems. The intricacies involved in aligning ILM with various software applications and IT infrastructures demand substantial IT expertise and time. Organizations often face challenges in ensuring seamless data flow and synchronization across platforms, which can impede operational efficiency and increase vulnerability to security breaches.
Data Privacy Concerns
With the increasing focus on data protection and privacy regulations, such as GDPR, tech companies face the critical challenge of ensuring compliance. Managing vast amounts of personal and sensitive data requires robust privacy measures to prevent unauthorized access and data breaches. Failure to adhere to these regulations can result in severe penalties and damage to a company’s reputation.
Scalability Issues
As tech companies grow and their user bases expand, the scalability of ILM solutions becomes a pressing concern. Adapting these systems to accommodate new users and technologies necessitates continuous updates and infrastructure investments. Organizations must ensure their ILM strategies are flexible enough to scale efficiently without compromising performance or security.
Unique Challenges Faced by Tech Companies in ILM
Technology companies encounter a distinctive set of challenges in Identity Lifecycle Management due to their inherently dynamic nature and rapid growth trajectories.
Rapid Expansion
One key issue is the onboarding and offboarding processes for employees, contractors, and partners, which are often more complex in tech industries due to the distributed, global workforce. Ensuring seamless and secure access management while accommodating remote work arrangements requires robust automation and real-time updating of identity databases.
Broad Software Integrations
Additionally, tech companies frequently integrate with a multitude of third-party applications, necessitating advanced inter-system compatibility and secure data sharing protocols to prevent unauthorized access and data breaches.
Software Development Challenges
Moreover, the fast-paced development cycles in tech companies introduce a continual flux of user roles and permissions that complicates identity governance. As tech companies strive to innovate and deploy new features rapidly, maintaining alignment between development teams and IT governance processes becomes critical.
There is also the persistent challenge of balancing security with user productivity, as tech professionals often require access to a vast range of tools and environments. Successfully navigating these issues demands a tailored ILM strategy that is adaptable, scalable, and integrates seamlessly with evolving technologies.
Keys to Success in Setting Up ILM
The challenges of implementing a successful ILM program can be overcome by focusing on a few critical areas.
Automation
Incorporating automation into ILM strategies significantly enhances their effectiveness and efficiency. Automation facilitates the streamlined management of user identities throughout their lifecycle, reducing the manual workload on IT departments. This is particularly beneficial in handling repetitive tasks such as provisioning, deprovisioning, and role assignment, which are prone to human error if performed manually.
By leveraging automated workflows, organizations can ensure that access rights are consistently updated in real-time, maintaining compliance with security policies and reducing the risk of unauthorized access. Furthermore, automation supports scalability by enabling the seamless addition of new users and systems without compromising the integrity or speed of identity management processes. Ultimately, adopting automation not only optimizes operational efficiency but also fortifies security postures, as policies can be enforced uniformly across the entire enterprise.
Upfront Planning
To navigate the complexities of ILM implementation, comprehensive planning is essential. A well-structured plan ensures that all aspects of the ILM process are covered, from data governance to system integration, facilitating a smoother transition and reducing the risk of disruptions. For example, a strong ILM process will include information gathered about each role in the company, so that when a new onboarding occurs, the new member of the workforce can have access to only the systems and services they need.
Continuous Monitoring and Improvement
The dynamic nature of cyber threats and technological advancements necessitates ongoing monitoring and improvement of ILM systems. Organizations must adopt a proactive approach, continually assessing and updating their ILM strategies to combat new threats and leverage emerging technologies. Regular training and awareness initiatives can also empower employees to recognize and respond to security challenges effectively.
Partner with Montra for ILM Excellence
Identity Lifecycle Management is an integral component of modern IT strategies, offering substantial benefits in security, compliance, and operational efficiency. By addressing key challenges and implementing effective strategies, tech companies can maximize the advantages of ILM and drive long-term success.
Embarking on your ILM journey requires expertise and precision. Montra stands ready to guide your organization through the complexities of ILM deployment, ensuring robust security measures and seamless integration with your existing systems. Our unique software and our team of experts is committed to tailoring solutions that meet your unique needs, helping you achieve compliance and operational efficiency. Contact Montra today to learn how our solution can uniquely support you in securing and managing your digital identities effectively.
Reach out to us at info@montra.io or visit our website for more information on how we can help you succeed.