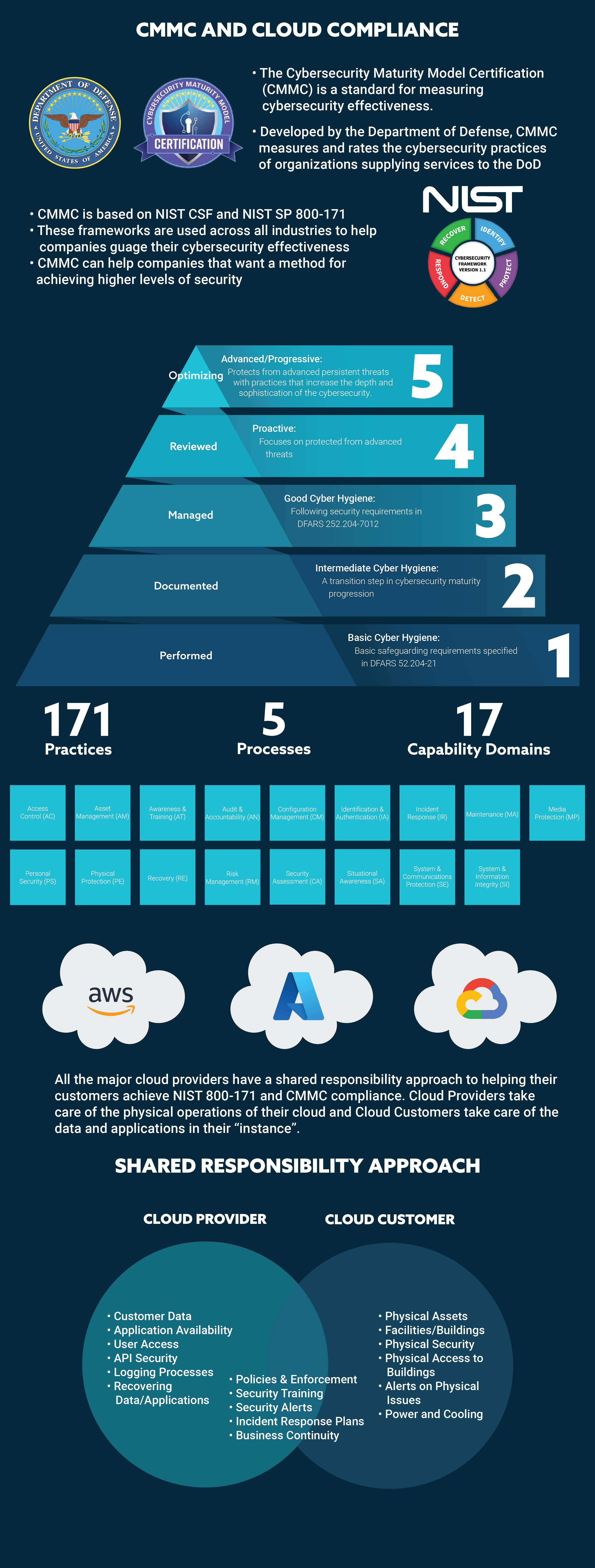
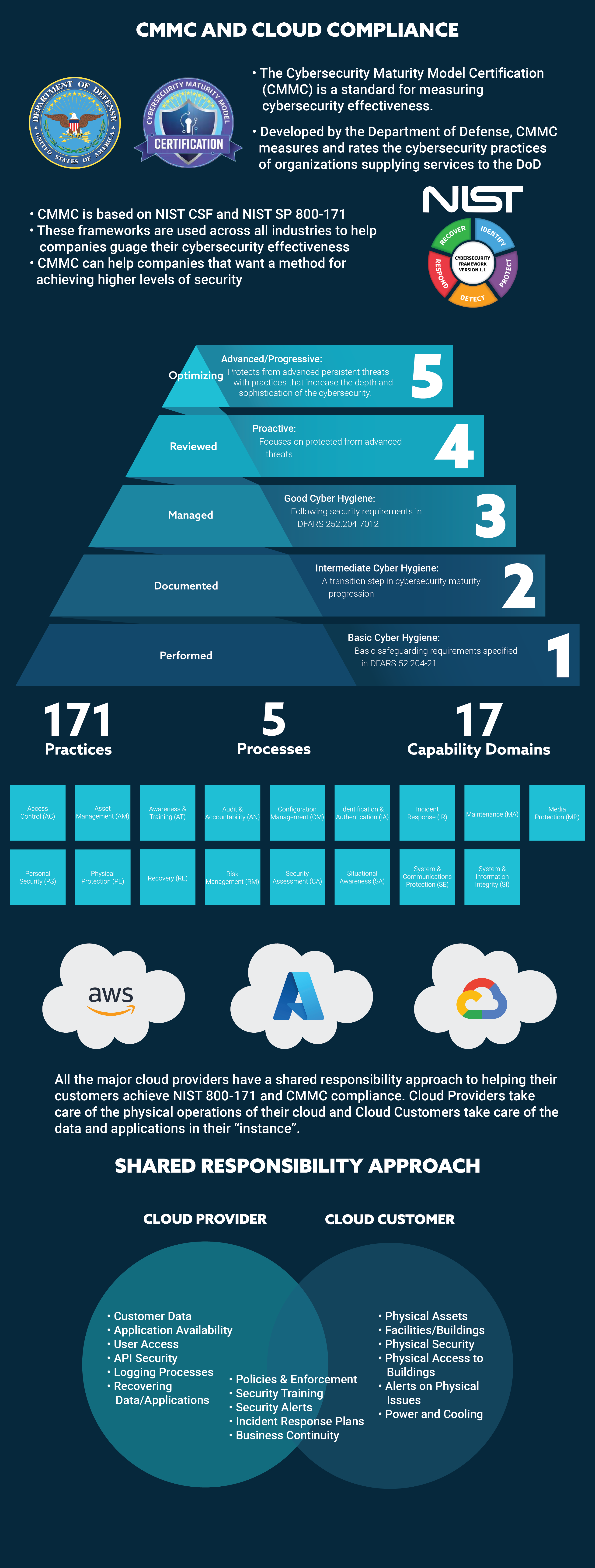
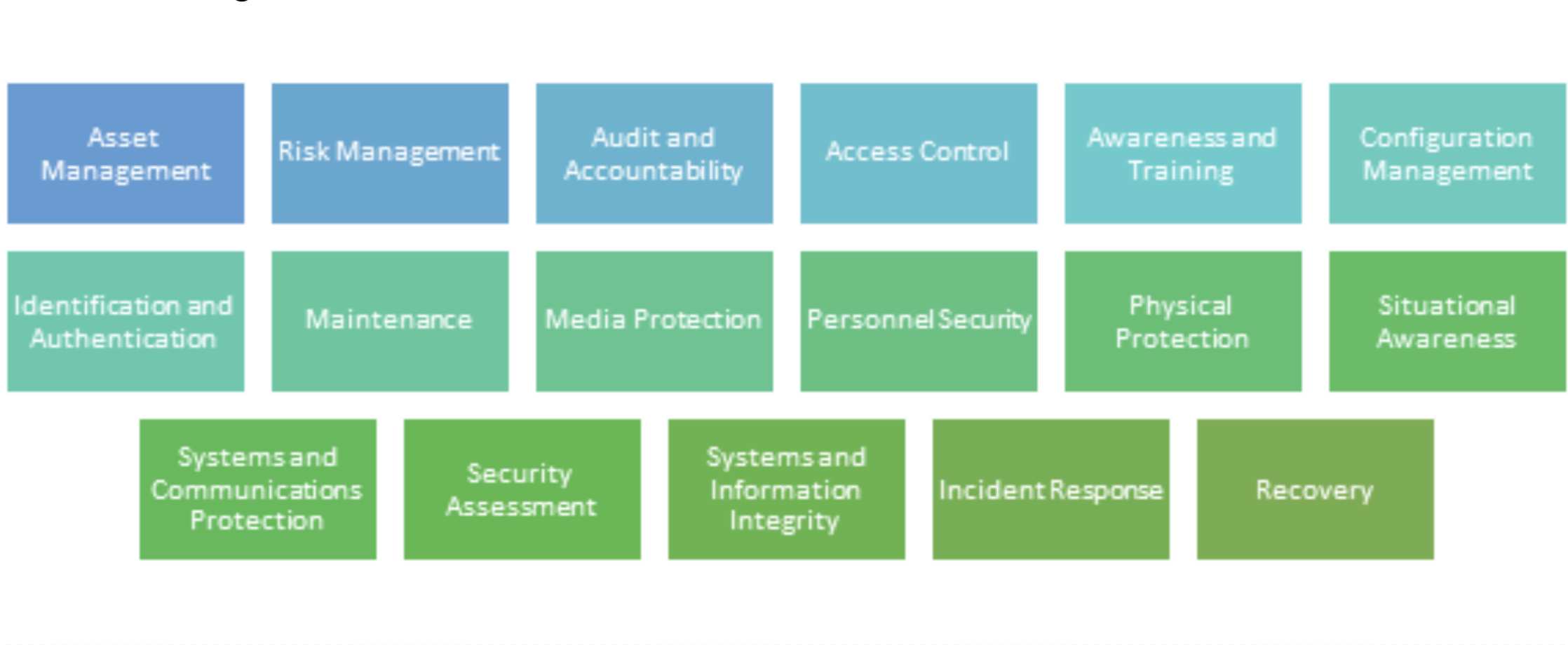
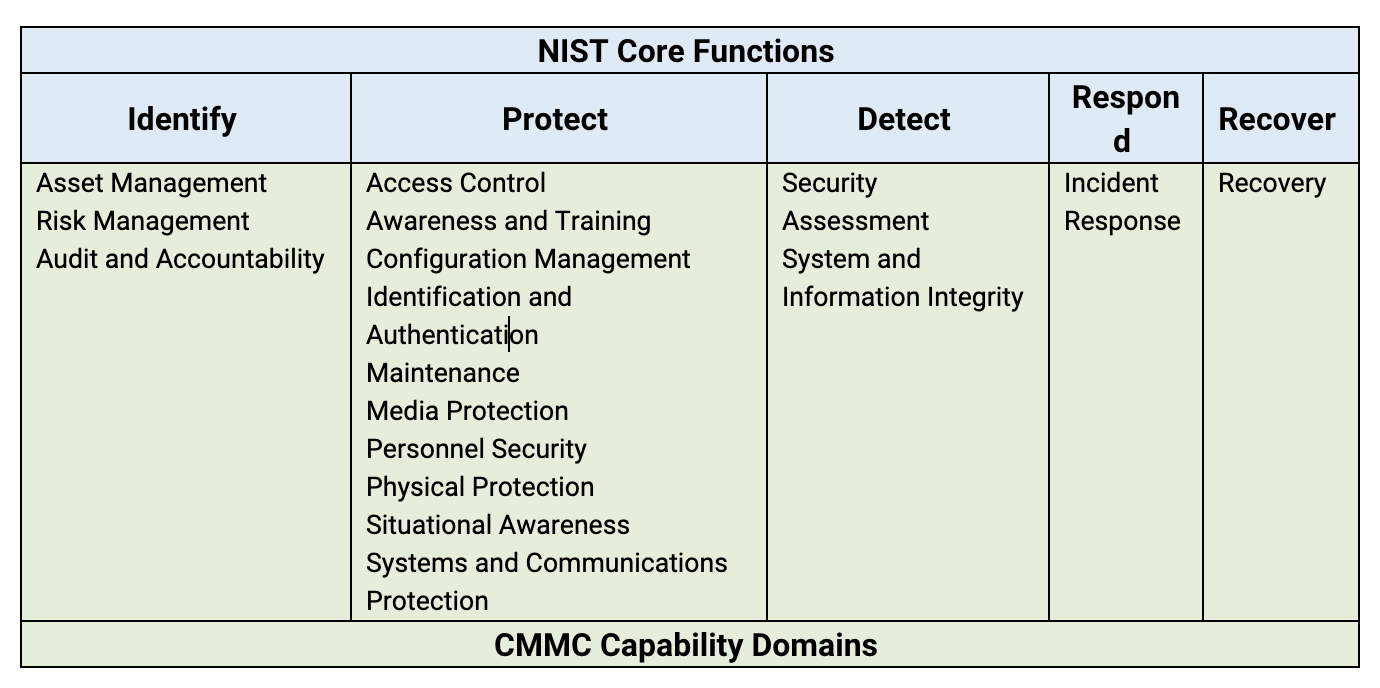
Unless you work for a very large organization that can cost justify developing and maintaining a private cloud infrastructure, utilizing Cloud technologies will mean relying on one or more public Cloud Service Providers (CSPs).
Recent high-profile data breaches have brought the risks associated with storing personally identifiable information (PII) into the limelight (i.e., the 2017 Equifax breach, the 2019 CapitalOne breach). Yet, the question of who is ultimately responsible for regulatory compliance remains a significant area of confusion. According to a recent study, only 39 percent of IT decision-makers considered themselves responsible for the compliance of data stored on cloud services. This is an incredibly dangerous mindset to possess, as by law, the ultimate responsibility for regulatory compliance remains firmly in the hands of the data owner – not the CSP.
Which Compliance Regulations Matter in the Cloud
The cybersecurity and data privacy compliance regulations that affect your company are dependent upon the industries in which you operate. Examples include federal government (FedRAMP), manufacturing (GMP), healthcare (HIPAA), real estate (CFPB), and financial services (FINRA, NYDFS). So, which regulatory requirements do you have to worry about in the cloud? The simple answer is the same ones that apply to your business already. Depending on your company’s industry, geographic location, and business function, this could be a range of compliance regulations, including:
- National Institute of Standards and Technology (NIST)
- General Data Protection Regulation (GDPR)
- California Consumer Privacy Act (CCPA)
- Health Insurance Portability and Accountability Act (HIPAA)
- Financial Industry Regulatory Authority (FINRA)
- Payment Card Industry Data Security Standard (PCI-DSS)
- Federal Information Security Management Act (FISMA)
- Sarbanes-Oxley Act of 2002 (SOX)
It is important to understand how your data and processes within your cloud service are affected by all of the applicable regulations, including data storage and retention policies, user access and password policies, and Most of these compliance frameworks require periodic testing of your IT operations, as well as ongoing monitoring to ensure constant It is important to understand the requirements While the responsibility for maintaining compliance lies solely within your organization, you don’t have to take on this burden completely alone. The good news here is that a consultant or managed IT services provider can guide you through the compliance challenges to meet the necessary laws and regulations.
When it comes to ensuring that your cloud operations will be in compliance with the regulatory requirements of your business, here are a few key tips…’
4 Tips for Ensuring Compliance in the Cloud
1. Realize a Compliant Provider Will Not Make You Automatically Compliant
Depending on which regulation you are subject to, you may be required to use a cloud service provider that is certified with those regulations. But it is important to note that using a compliant provider does not in and of itself make your business compliant automatically. You still have to use the service in a compliant manner; it is your responsibility to ensure the provider maintains regulatory controls on an ongoing basis. And you still have to maintain compliance for your own IT operations which connect to the cloud service provider.
2. Know Where Your Data Will be Stored
Some compliance regulations have geographic restrictions on where certain types of data can be stored and processed. For example, the European Union Data Protection Directive requires personal data to remain within the borders of the EU or a third-party country that offers adequate protection based on their previously defined security standards. This can pose a very large challenge if your CSP operates data centers and stores your data around the world. There is good news here: being aware of this caveat is a large part of the battle. All reputable cloud service providers are aware of this issue and offer geographical nodes that customers can select for their data to reside in as a part of their service offering.
3. Understand Access Control
A large portion of regulatory IT compliance stems from ensuring proper controls are in place over who has access to what data in the system. During a compliance audit, you must be able to prove the level of access that each user has and how those various levels are maintained. Your CSP must be able to provide you with documentation outlining how the implement separation of duties for administrative functions. They must also be able to provide clear documentation showing which users had access to which systems when, and what data and systems were able to be accessed by each user.
4. Know Your Service Level Agreement (SLA)
Regardless of what compliance regulations you are subjected to, don’t assume your CSP’s terms and conditions will satisfy your requirements alone. You should know the details and fine print of your cloud services contract inside and out. Again – the sole responsibility of compliance in the cloud is ultimately up to you, not your provider. Your SLA should be very clear on roles and responsibilities, incidence response execution, and data breach remediation. Everything in the SLA must be in accordance with the regulations governing your business. The finer points of an SLA are able to be negotiated with the service provider before signing. Just don’t wait until you have signed to realize that all your bases are not covered.
The good news about ensuring compliance within your Cloud environment is that legitimate service providers will be able to provide the right service for you to meet your governing regulations. That said, you need to know how to apply the regulations properly to how you are using the cloud service. If you are concerned about your regulatory compliance in the cloud services you are using, we recommend bringing in a 3rd party IT service provider, such as Montra.
Montra’s cloud experts can examine your current cloud operations, navigate you through the best options for establishing full compliance, as well as monitoring your compliance over time.
For more information about how Montra can help with your cloud compliance, contact us today.