CMMC and Cloud Compliance for Mid-Market Companies
The Cybersecurity Maturity Model Certification (CMMC) is a new and still developing standard for measuring a company’s cybersecurity effectiveness. It has been developed by the Department of Defense to measure and rate the cybersecurity practices of the Defense Industrial Base (DIB) who are supplying services to the DoD.
While the CMMC only applies to DoD contractors, it is based on NIST CSF and NIST SP 800-171. These NIST frameworks are used across all industries to help companies gauge their cybersecurity effectiveness. CMMC combines NIST and other standards into a unified standard for cybersecurity, which can be applied to any company that wants to method for achieving higher levels of cybersecurity over time.
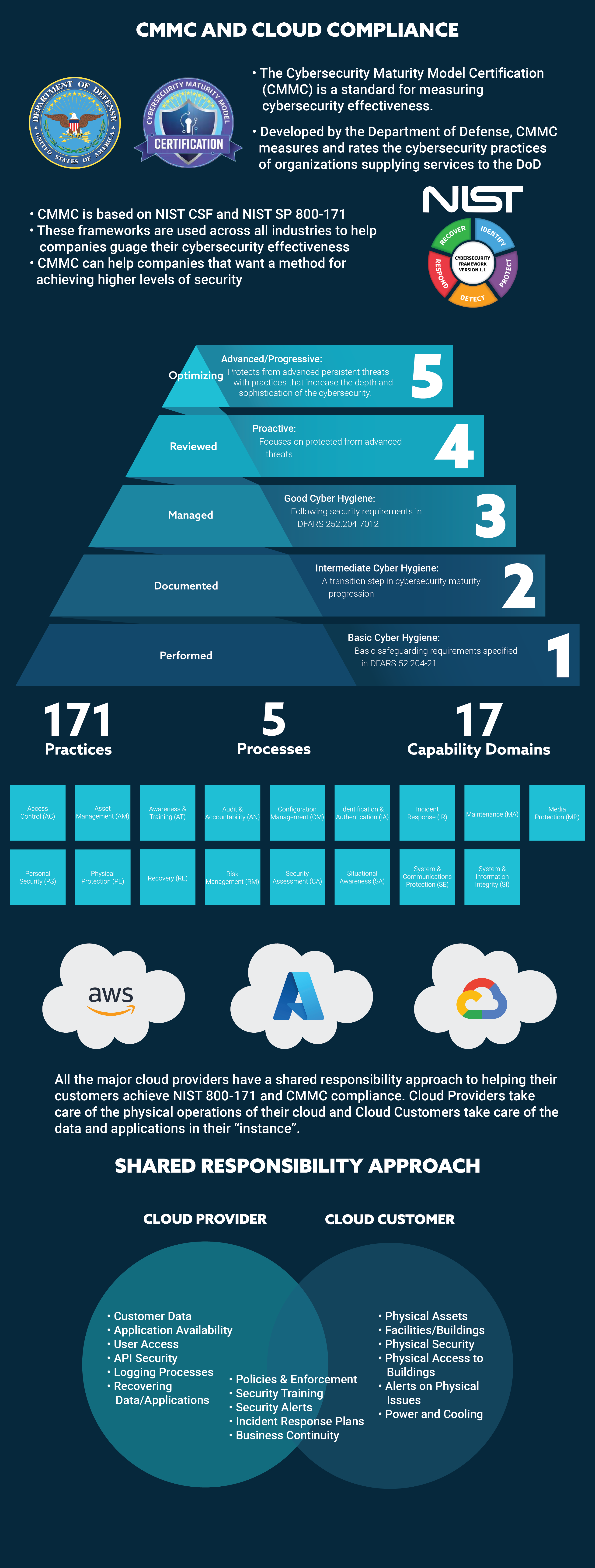
CMMC is simply divided into five levels to allow organizations to put measures in place to reach the minimum cybersecurity necessary to protect customer data. The addition of a third-party audit organization (3PAO) certification provides proof that any organization working to achieve a certain CMMC level has the proper security measures in place.
The five maturity levels range from “Basic Cybersecurity Hygiene” to “Advanced/Progressive.” Each maturity level includes progressively more demanding process and practice requirements to achieve the certification level.
Click To Download
Most mid-market and SMB companies will never need to go beyond Level 3 in the CMMC model unless they are doing work for the Federal government or another customer that maintains highly sensitive data and processes.
In addition to the level, there are 171 practices and 5 processes across the five levels of CMMC maturity. These practices and processes are organized into 17 capability domains to make them more manageable.
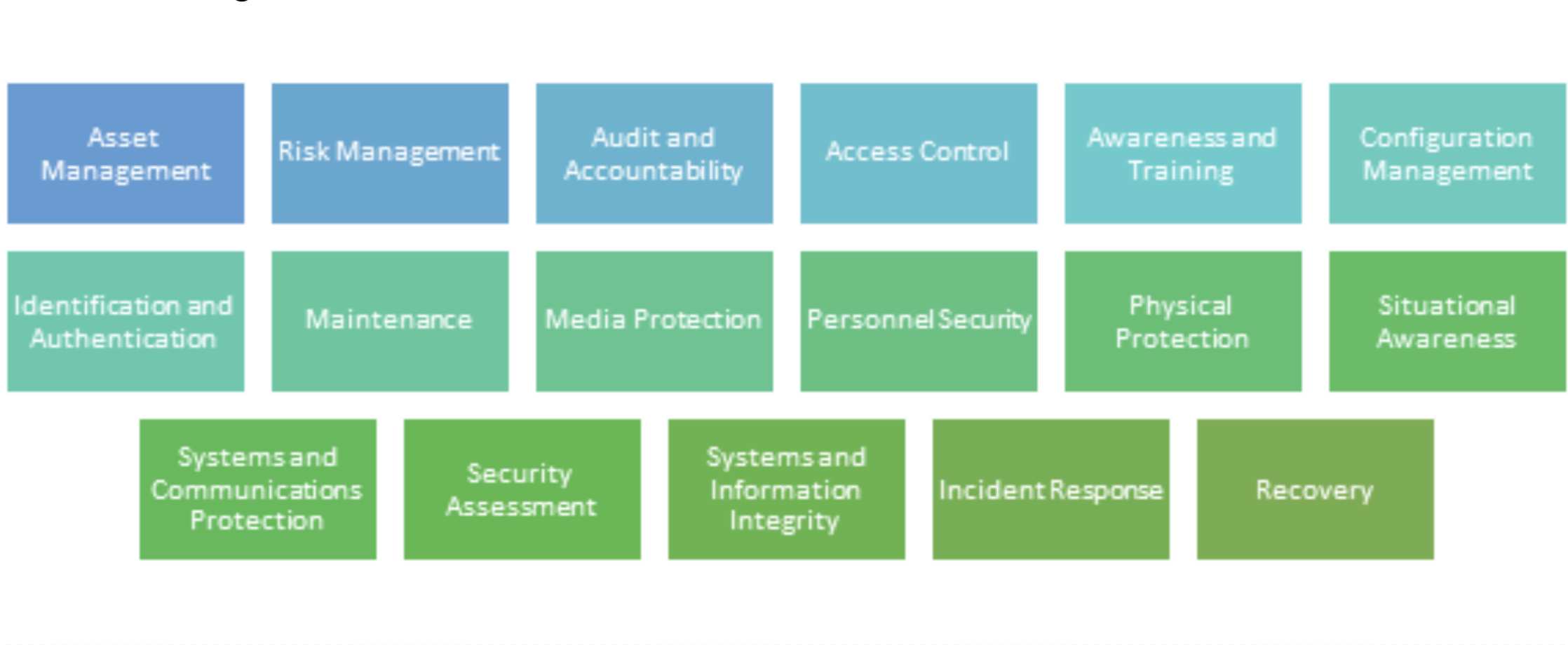
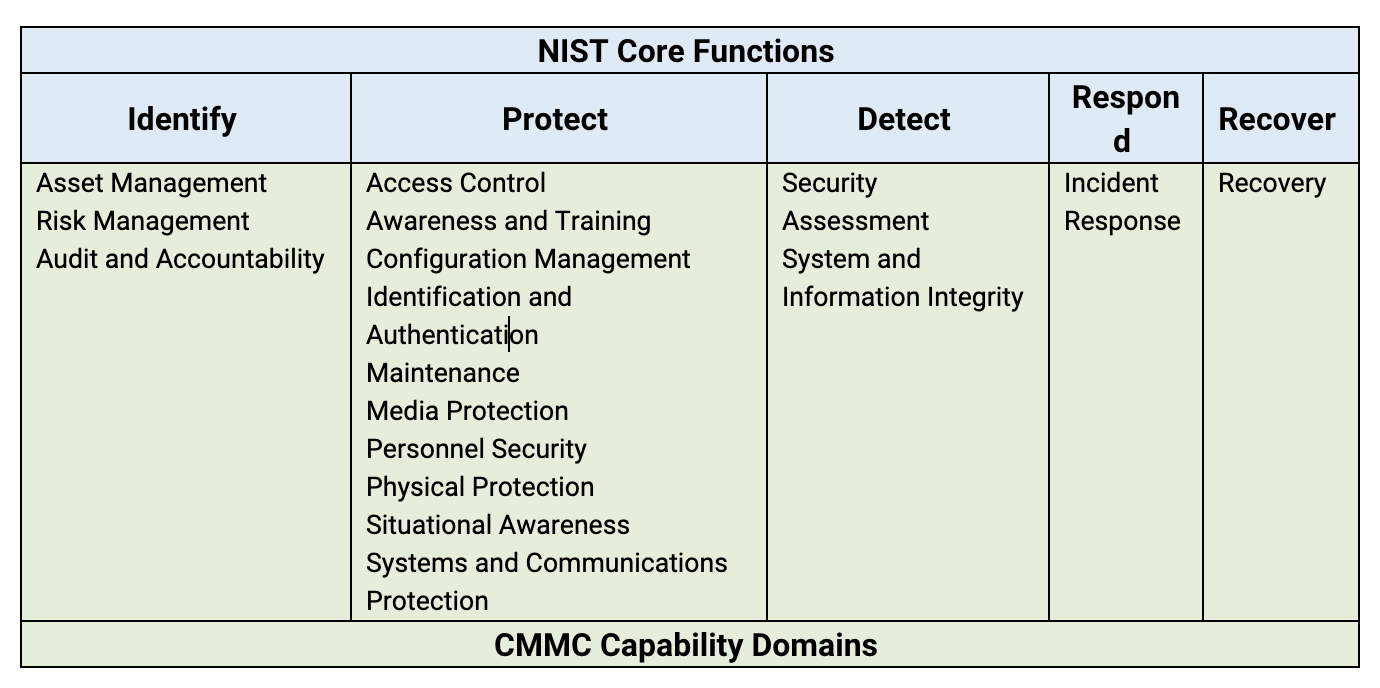
Looking at the number of practices and the capability domains can seem daunting. Since the CMMC and NIST are highly related, you can organize the CMMC Capability into the NIST Core Functions and then think about how you manage your cloud compliance to the CMMC levels by the functions.
CMMC and the Cloud
Since most mid-market companies are moving or have moved all their IT operations to the cloud, it is helpful to think of the CMMC in that context. If you move all your IT operations to the cloud, do you even need to worry about cybersecurity maturity? The answer is “yes”, but the good news is that the cloud and SaaS providers with whom you work will take on much of the cybersecurity burden and make achieving higher levels of CMMC easier.
Looking at the following table, you can see that moving to the cloud allows a company to “outsource” much of its burden of CMMC requirements to the cloud provider. It is important as you look at a cloud or SaaS provider to know whether they are CMMC compliant themselves. You can use this as a framework to analyze whether they are following the necessary steps to be a partner in your CMMC success.

CMMC compliance of cloud operations is very achievable for mid-market companies. The key to success is breaking the compliance process into smaller pieces and setting goals for achieving each level. Working with a company that can help you manage the project and work through implementing the needed security standards can make the process much easier and the likelihood of the success of the program much higher.
