Cloud Compliance in 2022
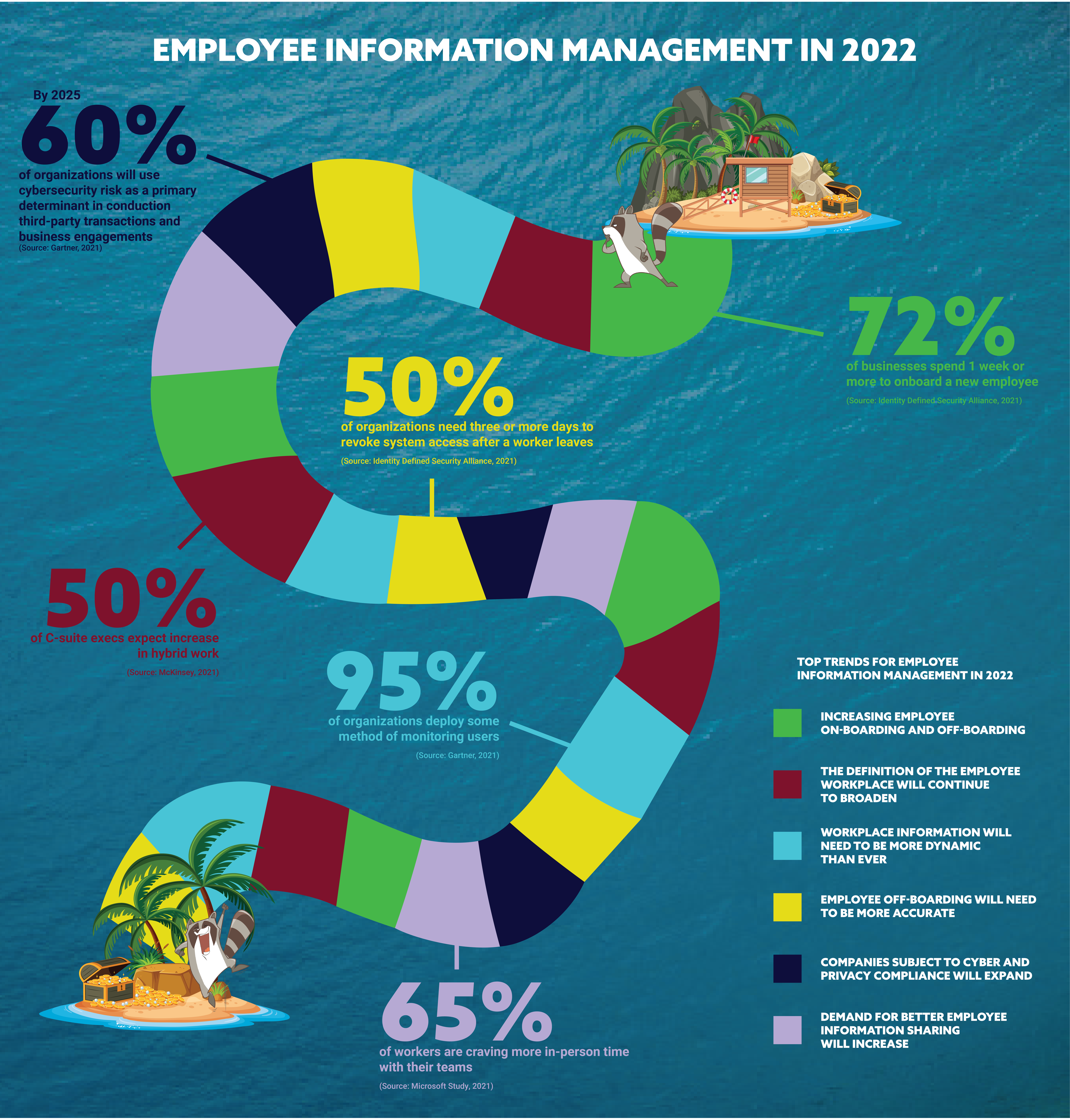
This is the second in our series of 2022 trends. Last week we covered employee information management trends for 2022. This week we look at the trends for cloud compliance in 2022.
Compliance – which in our context is specifically cybersecurity compliance – continues to be the way in which cybersecurity is managed and measured in modern IT. This is especially true is cloud services, where compliance standards have been an enabler to cloud growth. Cyber compliance standards like HIPAA, PCI DSS, NIST, and ISO 27001, help set the standards that businesses can use when evaluating how secure the cloud services are that they are evaluating and purchasing.
As the nature of cybersecurity attacks change, so too do the standards for cybersecurity compliance. This leads to our big trends in cloud compliance for 2022.
1. Companies Will More Broadly Apply CMMC to Their Non-Federal Clouds
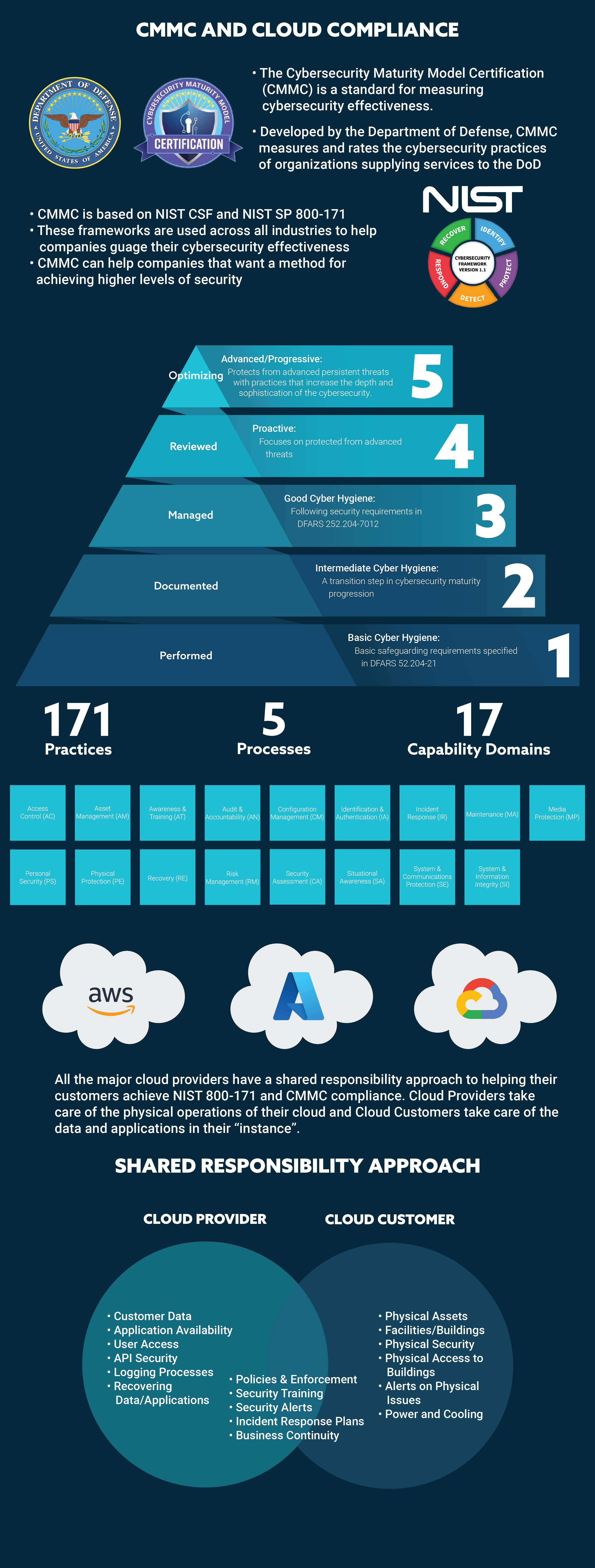
We discussed Cybersecurity Maturity Model Certification (CMMC) in a post a couple of weeks ago. This measurement standard from the Federal government will continue to expand into and provide influence over cybersecurity in the private sector.
CMMC incorporates NIST SP 800-171 standards and provides a convenient five-level maturity measure. This type of measure has been used in IT in the past with the Capability Maturity Model (CMM) which was used by many CIOs in the early 2000s to measure their path toward better IT process and service orientation.
With the recent announcement of CMMC 2.0, and with the prevalent knowledge of consultants that can lead IT organizations down the path of better cybersecurity, 2022 looks to be the year that CMMC measurement and reporting of the cloud becomes commonplace.
2. Private-Public Hybrid Cloud Models Will Add Compliance Nuance
In 2022, more companies will generate more of their data in the public cloud. Many of those companies will have policies to move portions of that data to their private cloud within defined periods of time. Which data is moved and when and where will continue to be a compliance challenge both for security as well as privacy. As compliance rules shift – like frequency of vulnerability scanning – companies that maintain hybrid clouds will need to update their procedures in both private and public contexts as well as the reporting for audits. Enforcement of data-related policies such as right to erase personal data will increase
3. Multi-cloud Application Compliance Will Become More Complex to Track
When companies implement applications in a cloud today, they mostly isolate each application in one cloud – typically called hybrid cloud. Multi-cloud applications span more than one cloud and are increasing in popularity as different cloud vendors develop specialized and unique services. In 2022, more companies than ever will be using multiple clouds for a single application.
For instance, maybe you develop a customer relationship management application for your sales team. You might store customer phone numbers in one cloud because their database service has privacy protections built-in, but you use a slick emailing app from another cloud that is easy to implement and extend. When emails and first names are temporarily stored in the second cloud, there becomes a second location for personally identifiable information (PII) to reside. Privacy policy understanding and enforcement is needed in both clouds, but without a rather technical review of each component of the application, this can be missed.
Compliance audits and policy enforcement will need to get increasingly into the “weeds” on each application to understand where the cyber-risks are and how cyber-compliance policies apply.
4. Compliance Ownership When Using Cloud-native Services Will Shift
All the major clouds – AWS, Azure, GCP, IBM – have co-management models for cloud compliance, but the policies are mostly utilized for first-gen cloud technologies like virtual machines. The differences in co-management of cloud compliance with cloud-native services have been treated as a special case by cloud providers. In 2022, the prevalent usage of cloud-native services will make it necessary for cloud providers to address the ambiguities of cloud compliance responsibilities that these services create.
For example, with virtual machine implementations, responsibility for user credentials is clearly on the side of the customer. With cloud-native services, though, user credentials are exposed as they are used to access various services and/or are passed between services. How the user credentials are being handled by the cloud provider becomes important for compliance and security purposes for the cloud customer.
What do you think about cloud compliance in 2022? What are your big concerns for the upcoming year? Let us know what you think at info@montra.io.