Montra Receives 2025 TMC Future of Work Award
Montra Technologies Receives 2025 Future of Work Employee Experience Achievement Award
Via Workforce Manager recognized for advancing the modern workplace through employee-first innovation
ATLANTA, GEORGIA, (January 3, 2026) — Montra® Technologies announced today that TMC, a global, integrated media company, has named Via Workforce Manager as a recipient of a 2025 Future of Work Employee Experience Achievement Award.
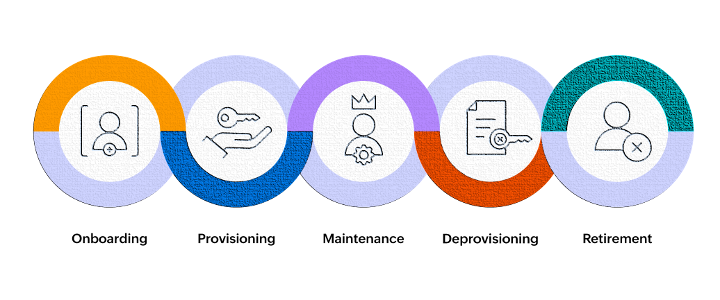
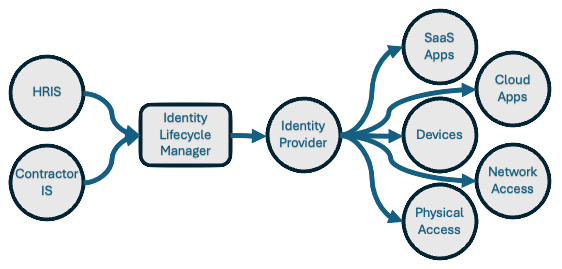
Via Workforce Manager is a unified identity and device lifecycle management (UIDLM) platform designed for mid-market IT and managed service providers. Via automates onboarding, offboarding, SaaS access, device management, and logistics in a single system which eliminates information silos between systems for identity, applications, and assets.
“This recognition reinforces our belief that employee experience and security should never be at odds,” said Scott Ryan, CEO at Montra. “With Via, we’re helping HR eliminate the friction of identity and access setup so employees can be productive on day one, while IT maintains control, security, and compliance. We’re honored to be recognized for advancing the future of work.”
“It is my pleasure to recognize Montra with a 2025 Future of Work Employee Experience Achievement Award for its commitment to customer service by focusing on employee-first innovations,” said Rich Tehrani, CEO, TMC. “In the opinion of our judges and editorial team, Montra has proven that a focus on their valued Team Members is driving better business results,” added Tehrani.
The winners of the 2025 Future of Work Employee Experience Achievement Awards will be featured on TMCnet.
For more information about TMC, please visit www.tmcnet.com.
About Montra Technologies
Montra Technologies is a managed IT services and solutions company delivering secure, scalable technology operations for modern organizations. From identity and access management to device lifecycle management, SaaS governance, security, and compliance, Montra simplifies IT so businesses can focus on growth.
Montra combines decades of enterprise IT expertise with modern, intelligent automation to reduce risk, improve security, and enhance the experience with technology across modern workforces. Learn more at www.montra.io and follow us on LinkedIn and X.
About TMC
For more than two decades, TMC has honored technology companies with awards in multiple categories — each among the most respected recognitions in the communications and technology industries. Winners represent leading organizations advancing innovation and driving growth across their markets. Every recipient is a verified leader, setting the benchmark for excellence in their field.
In addition, TMC provides global buyers with valuable insights to make informed tech decisions through our editorial platforms, live events, webinars, and online advertising. Leading vendors trust TMC, thought leadership, and our events for branding, thought leadership, and lead generation. Our live events, like the ITEXPO #TECHSUPERSHOW, deliver unmatched visibility, while our custom lead generation programs and webinars ensure a steady flow of sales opportunities. Display ads on trusted sites generate millions of impressions, boosting brand reputations. TMC offers a complete 360-degree marketing solution, from event management to content creation, driving SEO, branding, and marketing success. Learn more at www.tmcnet.com and follow @tmcnet on Facebook, LinkedIn, and X.
TMC Contact:
Stephanie Thompson
Manager, TMC Awards
203-852-6800
sthompson@tmcnet.com
Montra Contact:
Monty Rachleff
Marketing Manager
404-665-9675
mrack@montra.io
###