Identity Lifecycle Management in the Modern Enterprise: The What, Why and How
In today’s digital landscape, where data breaches and cyber threats are prevalent, businesses are increasingly focusing on Identity Lifecycle Management (ILM) to safeguard their sensitive information and ensure secure access control.
Understanding Identity Lifecycle Management
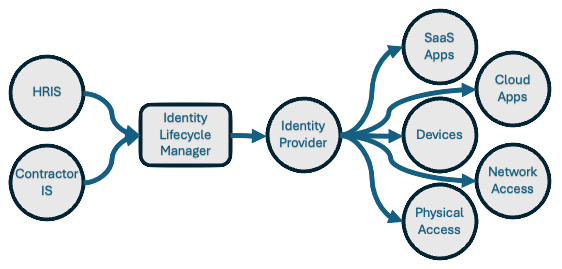
The Identity Lifecycle
Identity Governance enables organizations to strike a delicate balance between productivity – ensuring swift access to necessary resources for individuals entering the organization – and security – determining adjustments in access rights as per changes in employment status.
At the core of Identity Governance lies Identity Lifecycle Management, a crucial component for effectively managing digital identities. Scaling up governance successfully requires the modernization of the infrastructure supporting identity lifecycle management in applications. The objective of Identity Lifecycle Management is to streamline and automate the entire digital identity lifecycle process for individuals associated with an organization.
Identity Lifecycle Management encompasses the processes and technologies used by organizations to manage the lifecycle of user identities within their systems. It involves creating, maintaining, and revoking user access rights throughout the user’s journey with the organization:
-
Onboard: When a person requires access, applications require an identity. Hence, a new digital identity might need creation if not already existing.
-
Transfer: When someone transitions across boundaries necessitating adjustments to their digital identity by adding or removing access authorizations.
-
Offboard: When someone no longer requires access, it’s necessary to revoke access. Subsequently, the identity may become unnecessary for applications except for audit or forensic purposes.
Benefits of Implementing Identity Lifecycle Management
Implementing ILM offers several benefits to businesses including:
-
Security Enhancement: By enforcing access controls, it bolsters security measures to restrict sensitive data and system access solely to authorized users.
-
Administrative Efficiency: The solution simplifies user access management tasks, minimizing the chances of human error and unauthorized entry.
-
Compliance Maintenance: Additionally, ILM aids organizations in adhering to regulatory standards like GDPR and HIPAA, ensuring continued compliance.
Addressing Challenges with Identity Lifecycle Management
Businesses face challenges such as ensuring rapid onboarding and offboarding processes, and maintaining a balance between security and user convenience. ILM addresses these challenges by providing automated workflows for user provisioning and deprovisioning, role-based access control, and continuous monitoring of user activities.
Implementing Montra Via for Efficient Identity Lifecycle Management
To streamline the ILM process and ensure compliance, companies can leverage cutting-edge solutions like Montra Via. Via offers advanced features such as automated onboarding and offboarding of users, profile-based provisioning of user accounts on over 350 applications, direct integration with identity providers like Microsoft Entra and HR systems like ADP Workforce Now. By implementing Via, organizations can improve operational efficiency, enhance security, and reduce compliance risks.
Real-World Results
For instance, an Atlanta-based professional services firm implemented Via and received a 2x reduction in onboarding time and a 3x reduction in onboarding and offboarding mistakes within the first two months. They have improved the experience for their new employees who are getting productive faster, and they are reducing their security and compliance risks by ensuring “zombie” accounts aren’t left open after a departure.
Tips for Creating a Successful Identity Lifecycle Management Strategy
Creating and maintaining a successful ILM strategy requires more than just great software. Businesses need to change their processes and make certain their people have what they need to be successful. Any businesses should consider the following tips:
-
Balance Security and Accessibility: Strive to find a balance between stringent security measures and user-friendly access controls to ensure that users will follow the processes they should.
-
Security Awareness Training: Provide comprehensive training to employees on security best practices, data protection protocols, and the importance of adhering to ILM policies.
-
Rights Monitoring: Regularly monitor user access rights, review permissions, and conduct audits to identify and address any security vulnerabilities.
-
Seek Guidance: Keep abreast of industry trends, regulatory changes, and emerging technologies to adapt your ILM strategy accordingly. And if you need, find partners that can help you stay current.
By following these best practices, businesses can establish a robust Identity Lifecycle Management framework that safeguards critical assets, mitigates risks, and fosters a culture of proactive cybersecurity.
In conclusion, Identity Lifecycle Management plays a crucial role in modern business operations by ensuring secure and efficient management of user identities. By adopting advanced solutions like Montra Via and adhering to best practices, organizations can effectively navigate the complexities of identity management and safeguard their digital assets.
For more information about Montra, please contact us at info@montra.io.
Sources
- Identity Management Institute: “The Guide to Identity Lifecycle Management,” Identity Management Institute, 2022.
- Forrester Research: Jenkins, M., “The Role of Identity Management in Modern Security,” Forrester Research, 2021.
- Gartner, Inc.: Thompson, F., “Magic Quadrant for Identity Governance and Administration,” Gartner, Inc., 2022.
- U.S. Department of Health & Human Services: “Health Insurance Portability and Accountability Act (HIPAA) of 1996,” U.S. Department of Health & Human Services, 2020.
- European Commission: “General Data Protection Regulation (GDPR),” European Commission, 2022.
