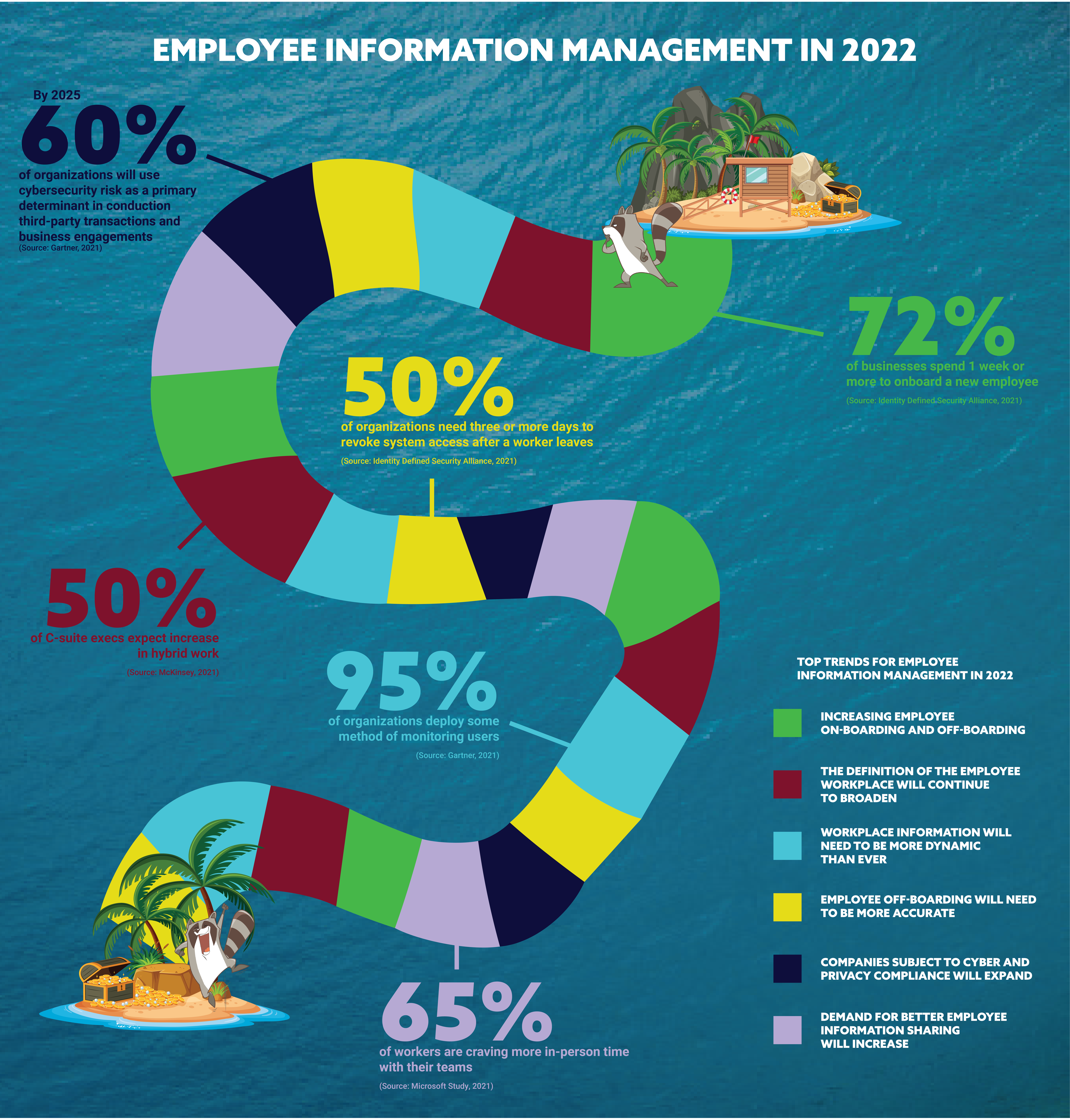
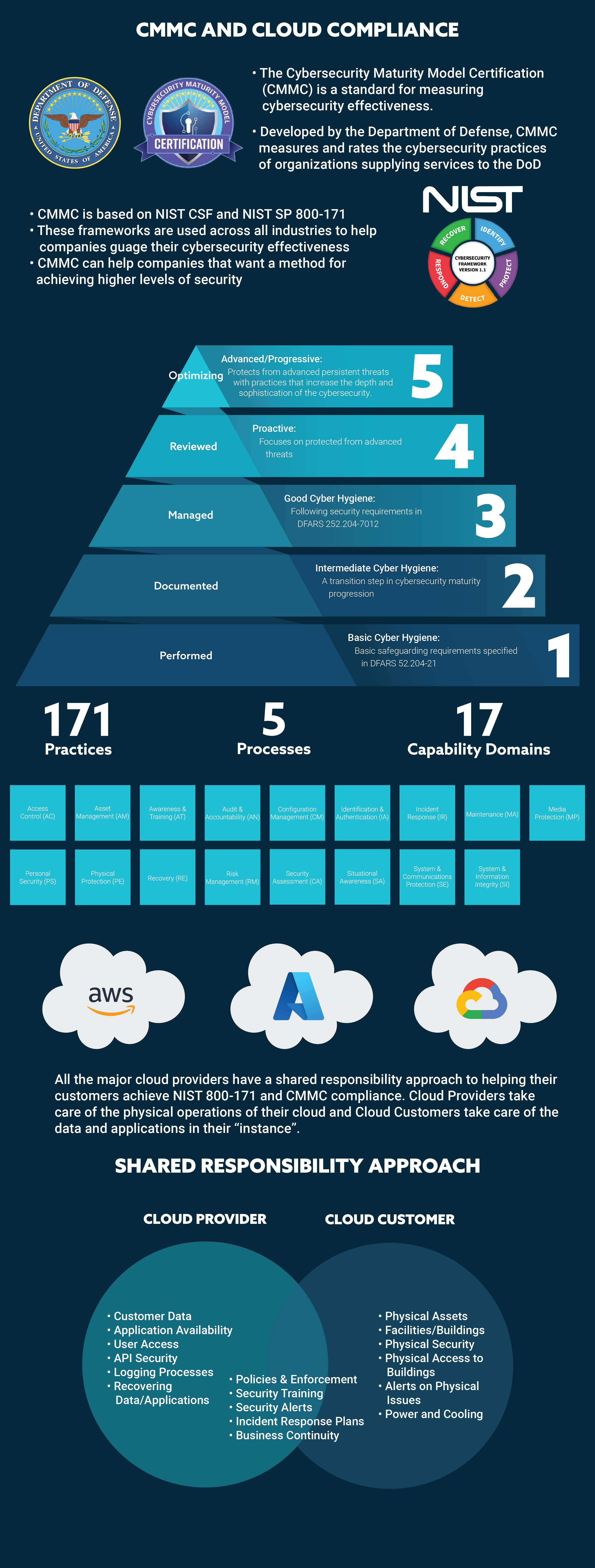
Checklist for IT Employee Offboarding
Whether an employee leaves a company of their own accord or not, they first must be offboarded to ensure an easy and secure transition from their current role to their next one. IT administrators play a critical role in the offboarding process and must quickly and efficiently off-board the employee to keep business running smoothly. Follow our nine-step checklist to make sure you’re protecting your company’s network and data.