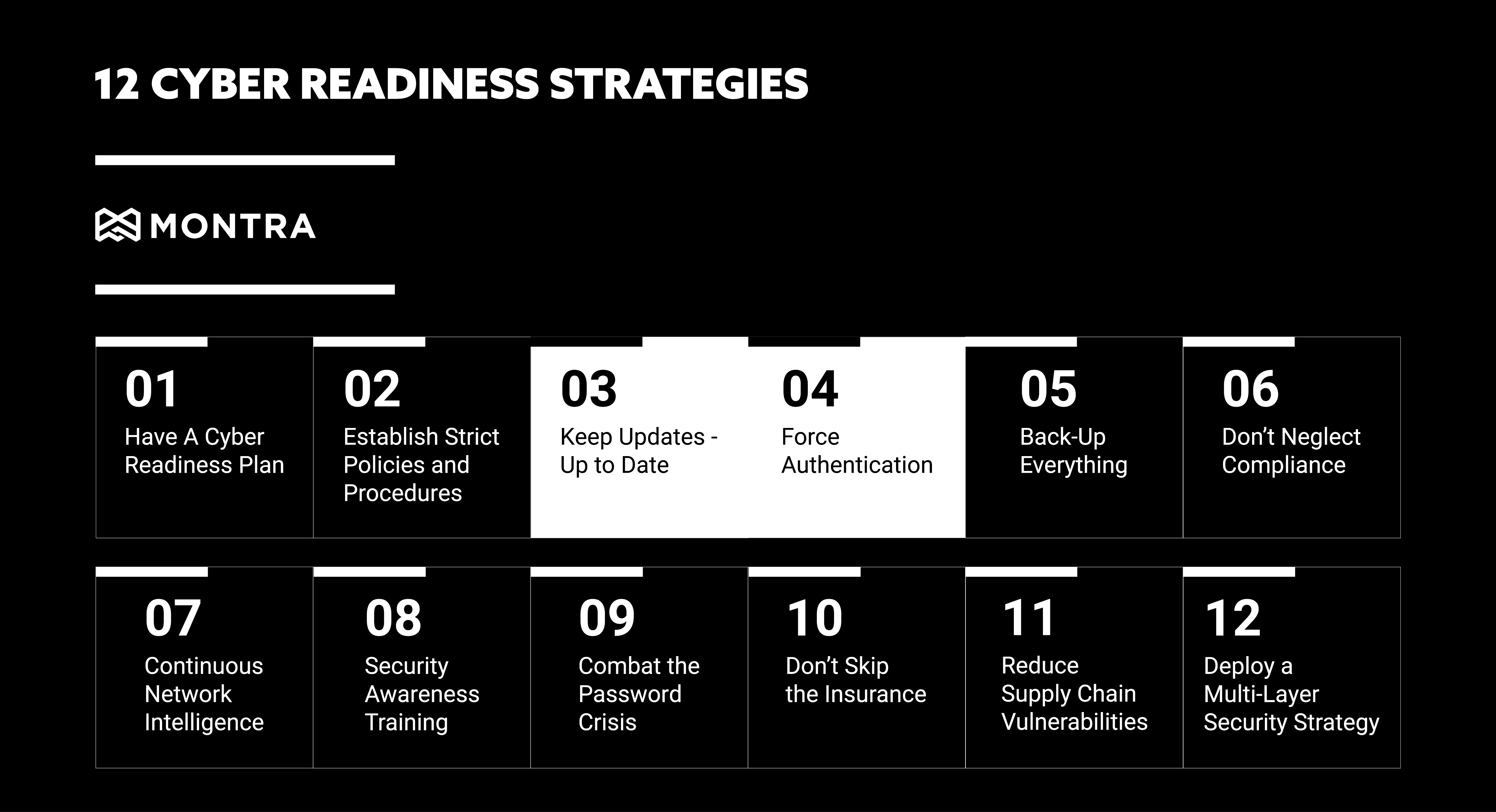
Seven Practices To Improve IT Asset Logistics
Do you know where all your company’s IT assets are? If not, you’re not alone – many businesses find it difficult to track down every phone, computer, or software license. IT asset tracking is an essential process for any organization looking to manage its technology resources efficiently. By establishing and following standardized procedures, your team can ensure that all devices and software are accounted for, and that important data is protected. In this blog post, we will outline some of the best practices in IT asset logistics so that you can create a system that works best for your organization.
IT asset logistics is the process of tracking, monitoring, updating, and securing assets throughout their lifecycle. This includes locating and identifying assets, recording and tracking changes to asset data, and maintaining security and control over assets.
The main goal of IT asset logistics is to ensure that organizations have a clear understanding of where all their assets are always. This helps to improve efficiency, reduce costs, and minimize the risk of lost or stolen assets.
For an organization to implement an effective IT asset logistics solution, there are several key requirements that must be met:
1. IT Asset Tracking Software: First and foremost, an organization needs appropriate IT asset tracking software. This software should be able to track every asset in the organization’s inventory, from laptops and smartphones to software licenses and cloud service subscriptions.
2. IT Asset Database: The IT asset tracking software should maintain a central database of all assets in the organization. This database should include detailed information about each asset, such as its make, model, serial number, and location. Not only does it provide a centralized repository for all data, but that data can also then be used to generate reports, conduct analysis, and track change over time. The asset database should be updated regularly to ensure that it is accurate and up to date. Additionally, the database should be accessible to authorized users only. This will help to ensure that sensitive information about assets is not compromised.
3. Device Tracking: The tracking software should be able to track the location of each physical device in real-time. This information can then be used to generate alerts if a device is moved without authorization, or if it goes missing. Additionally, the software should allow users to set up geo-fences so that they can be notified if a device enters or leaves a specified area. In some cases, it may also be necessary to attach tags to the IT device. These tags may use GPS or other technology to provide real-time locations for the IT devices, which can be useful for keeping track of high-value items or for monitoring device movements in real-time. Another common method is to use barcodes or RFID tags that can be affixed to devices and read using a handheld scanner. This data can be used to track the location of devices and keep inventory records up to date.
4. Reporting and Analytics: The reporting and analytics features of IT asset tracking software are key for understanding how assets are being used, where they are located, and other data points. These reports can be used to improve operational efficiency and optimize the utilization of assets.
For example, a report on IT asset usage can help to identify which assets are being used most frequently and which ones are sitting idle. This information can then be used to make decisions about how to best allocate resources. Additionally, reports on asset location can help to ensure that assets are being used in the most efficient way possible. If an asset is constantly being moved from one location to another, it may be time to consider investing in additional units so that the asset can be used more efficiently.
5. Integration: Finally, IT asset logistics software should be able to integrate with other business systems. This includes ERP, CRM, accounting systems, monitoring and security systems, and shipping and procurement services. Integration allows organizations to automatically share data between different business processes and improve overall visibility into their operations. Integration is key when it comes to effective IT asset logistics. All too often, organizations silo their information, making it difficult to get a holistic view of their technology resources. By integrating your IT asset tracking system with other tools and processes, you can ensure that everyone is on the same page and that important data is not lost in the shuffle.
6. Automation: There are two ways to use automation to improve the accuracy and efficiency of IT asset logistics. The first is to automate the data collection process. This can be done in several ways, such as with barcodes or RFID tags, which are scanned by a handheld device. This data can then be used to track the location of devices and keep inventory records up to date. Secondly, you can use automated alerts to notify the appropriate personnel if a device is moved without authorization, goes missing so that your employees can take corrective action immediately.
7. Standardization: The last and most important aspects of IT asset logistics is to establish standardized procedures. This will ensure that all devices and software are accounted for, and that important data is protected. By following a set of standardized procedures, your team can improve communication and collaboration, and make sure that everyone is on the same page. Additionally, standardized procedures will help to ensure that your tracking system is able to scale as your organization grows.
IT asset logistics is a critical process for any organization that relies on physical assets. By implementing an effective asset tracking solution, businesses can improve efficiency, reduce costs, and minimize the risk of lost or stolen assets. For more information on asset tracking, please contact us at sales@montra.io!