12 Cyber Readiness Strategies
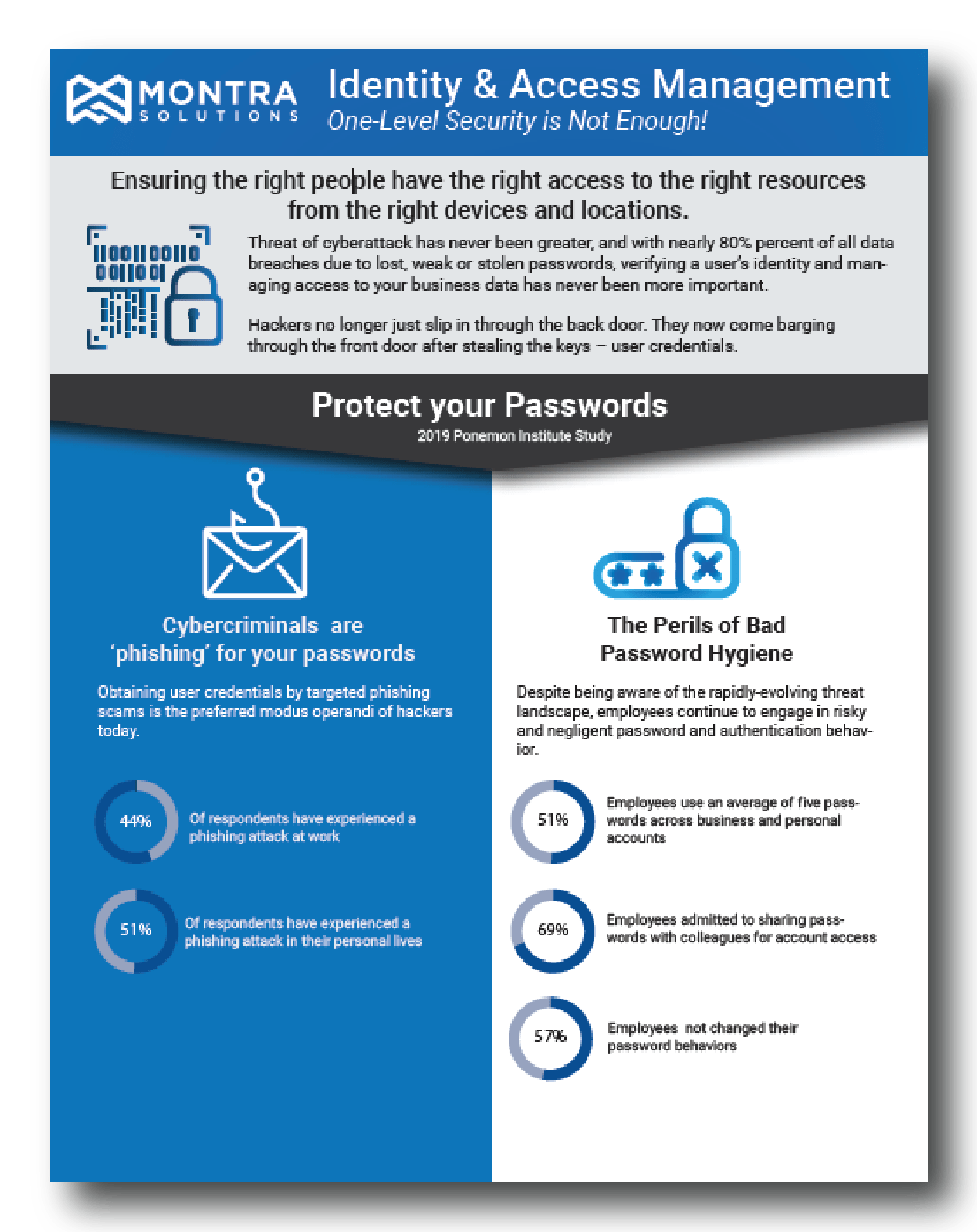
4. Force Authentication
One-level security is no longer enough. Even the strongest passwords are vulnerable to theft or exposure. Requiring more than one method to authenticate user identity or access permissions can reduce or eliminate the risk of stolen or unauthorized credentials being utilized.
Get cyber ready with identity and access management today.